An interview on our new research paper – A Novel Intrusion Detection System Against Spoofing Attacks in Connected Electric Vehicles
Dr. Leandros Maglaras was interviewed from Elsevier regarding a recently accepted article in Elsevier Array journal. In this paper, an Intrusion Detection System (IDS) based on supervised Machine Learning (ML) algorithms was developed to detect spoofing attackers and exclude them from the proposed system for Dynamic Wireless Charging of Electric Vehicles with the use of Mobile Energy Disseminators (MEDs), as a mitigation approach.
Why is this research important?
Transport is one sector that will experience significant change over the next few years, due to a number of factors including congestion and the drive for cleaner and environmentally friendly cities, combined with technological advances such as Electric Vehicles, 5G, and Artificial Intelligence. For such premise to materialise, it is necessary to consider the security argument and make sure that the Intelligent Transportation Systems, such as the one proposed in this work around Mobile Energy Disseminators (MEDs) for Electric Vehicles, is safe for the public to use at all times.
What is the novelty of the proposed method?
In the recently accepted article in Elsevier Array, Dr. Maglaras and his colleagues present an IDS based on ML that can detect spoofing attackers. Spoofing attacks are particularly dangerous since they can inject to the system falsified information that may affect critical aspects of its operation. Specifically, the presence of a spoofing attacker in the proposed Dynamic Wireless Charging (DWC) system, which consists of a MED and a Static Charging Station (SCS), increases the average travel time of Electric Vehicles (EVs) by 13%. This was our initial motivation for the development of a novel IDS that is able to secure the proposed mechanism. Based on the outcomes of the IDS, attackers are excluded from the Dynamic Wireless Charging mechanism. This is the ML-based IDS reported in the literature that can effectively detect a spoofing attacker in a realistic application, alleviating also its effects.
A significant contribution of our research is the introduction of a novel metric that is used as a separate feature for the ML algorithms. This metric named Position Verification using Relative Speed (PVRS) is based on the relative speed Δu which is estimated through interchanged signals in the PHY layer. PVRS compares the distance between two communicating nodes through their on-board Units (OBU) and the estimated distance that is calculated using the Δu value. The effect of the proposed PVRS metric in the performance of the probabilistic IDS was an increase of 6% in the detection accuracy which is a very significant improvement. One major contribution of our research to the literature is that our IDS uses a cross-layer approach, is based on passive V2V communication only and can be applied to a set of EVs without any extra cost for infrastructure such as the deployment of Road Side Units (RSUs).
Why is this research timely?
Two of the main prohibiting factors for the adoption of the Electric Vehicles (EVs) across Europe are the driving range (i.e. the distance the vehicle can cover before it needs to recharge), and the lack of supporting charging infrastructure. DWC is a technology with great potential, but further R&D may still be required towards its applicability. We recently proposed a novel solution that can be used in order to increase the driving range of EVs in which the city buses can act as energy sources on the move. Like most of DWC systems, it is based on wireless Vehicle-to-Vehicle (V2V) communications between EVs and MEDs and based on the position and the energy needs of each EV performs a route optimisation solution. Specifically, nodes that enter the system broadcast periodically beacon messages, known as Cooperative Awareness Message (CAM), to inform of their presence.
However, these messages are vulnerable to a wide range of cyber threats, such as eavesdropping, spoofing and modification attacks. In particular, a spoofing attack could allow an attacker to modify the charging process (e.g. changing the order of charging) either on a MED or on a Static Charging Station for its benefit, affecting legitimate EVs. A spoofing attack is one of the most dangerous attacks for route optimisation systems. This type of attack allows an attacker to spoof its real geographical position in the information sent within CAM messages, making other nodes believe that the vehicle is in another position. This way an attacker can benefit against competing EVs, since the charging sequence is based on optimal navigation decisions. Thus, the presence of an Intrusion Detection System (IDS) capable of detecting GPS falsification is essential in a DWC system.
It is exciting to see our research in cyber security, communications networks, AI/ML and Electric Vehicles come together to offer innovative solutions to problems that affect everyday life, whether it is the commute to work or living in a cleaner city. This research is a collaboration between De Montfort University, UK (Led by Dr. Leandros Maglaras), the University of Surrey, UK (Led by Dr. Sotiris Moschoyiannis) and University of Thessaly, Greece (Led by Dr. Antonios Argyriou). The leading researcher for this work is Dimitrios Kosmanos from University of Thessaly, expected to defend his PhD later this year. This research has been partly funded by the UK National Cyber Security Centre (NCSC) via a research exchange programme on VANS: Vehicular Ad-hoc Networks Security, the EIT Digital via the Real Time Flow project (GA no. 18387-SGA2018), the Innovate UK via the FLOURISH project (GA no. 102582)and the H2020 via the CONCORDIA project (GA no. 830927). We are now in the process of building a consortium that includes Academia and Industry in the field of Electric Vehicles and automation in order to test our innovative DWC and IDS mechanisms in real situations by conducting field trials.
In a nutshell
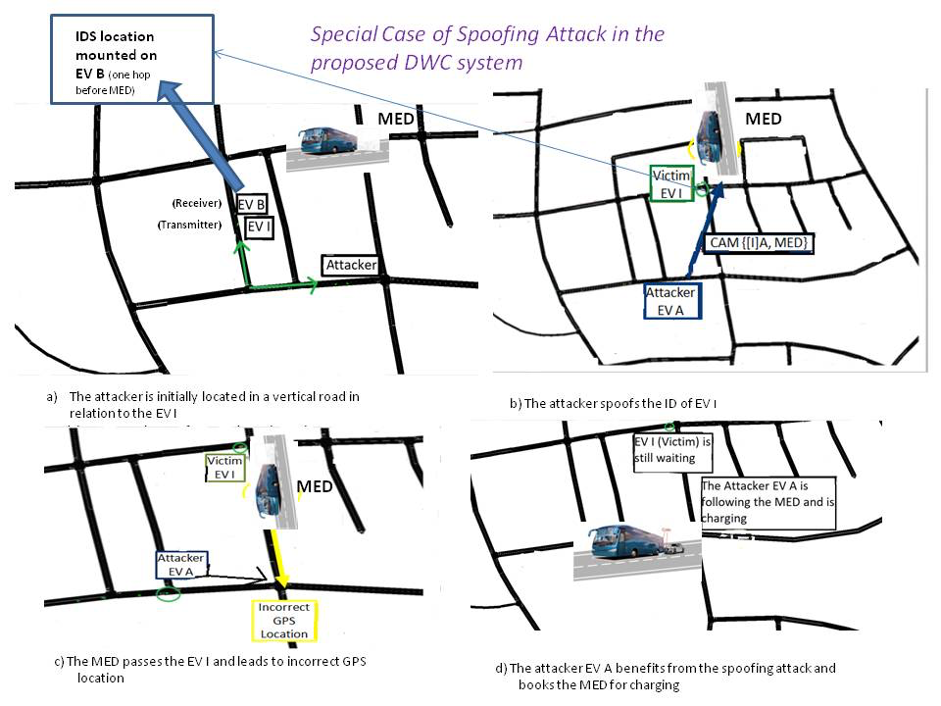
A specific example of the Dynamic Wireless Charging System that is susceptible to a spoofing attack is described in the Figure below. The EV A intercepts the ID of EV I (Fig.b). As a consequence of the spoofing attack, EV I loses its turn for charging (Fig.c) and the attacker EV A ends up following the MED for charging (see Fig. d). The proposed IDS is mounted on EV B as can be seen in Fig. a.
Leandros Maglaras, Securing a dynamic wireless charging system for electric vehicles, Array (2020)
Dimitrios Kosmanos, Apostolos Pappas, Leandros Maglaras, Sotiris Moschoyiannis, Francisco J. Navarro, Antonios Argyriou and Helge Janicke, “A Novel Intrusion Detection System Against Spoofing Attacks in Connected Electric Vehicles“, Elsevier Array, Vol. 5, March 2020, DOI: 10.1016/j.array.2019.100013