Benefits of Ecosystem approach to Cybersecurity Threat Intelligence Sharing
They always say time changes things, but in the case of threat intelligence sharing it actually does
CONCORDIA consortium of more than 50 partners, whose purpose is to lead the boosting Europe’s cybersecurity future, often regards itself as an “ecosystem”.
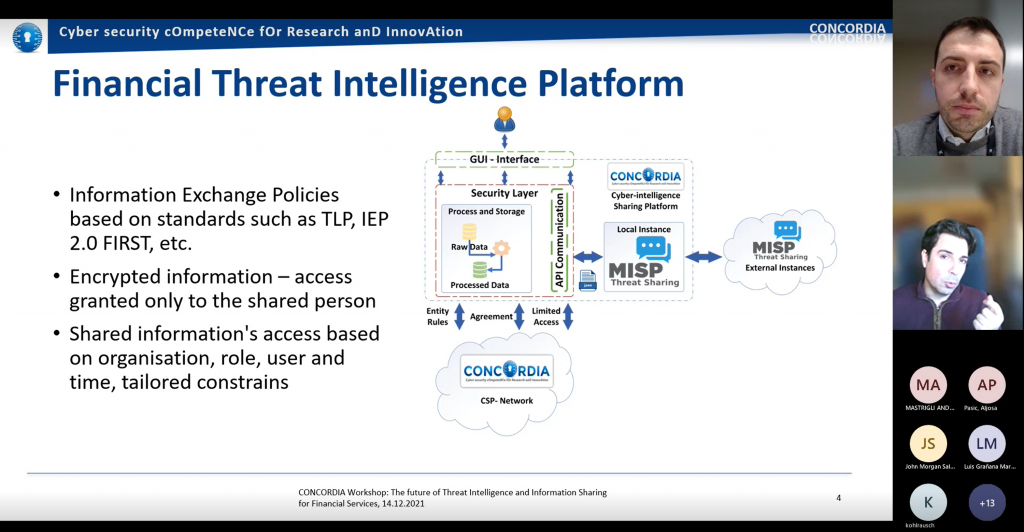
In the context of CONCORDIA we define ecosystem as “a system of people, practices, values, and technologies in a particular environment” (see CONCORDIA deliverable D6.3). The ecosystem includes roles, tasks, and relationships, which could be customized for different organisations, sectors, position in the digital supply chain, or even different EU regions or member states. Unlike the concept of a network, ecosystem also brings dynamicity and multi-disciplinarity, for example by an assessment of different alternatives from the economic perspective, which is done in CONCORDIA in WP4. Cost saving through “ecosystem approach” applies to reuse of software components, use of shared resources such data for lab testing, scaling-up or integration of new solutions, maintenance and evolution support by the open-source community, or development of solutions that rely on cooperation and collaboration, such as the case of cybersecurity threat intelligence sharing. In this blog, we focus on Financial Threat Intelligence Platform (F-TIP) and Financial Cybersecurity Threat Intelligence (F-CTI) process in general.
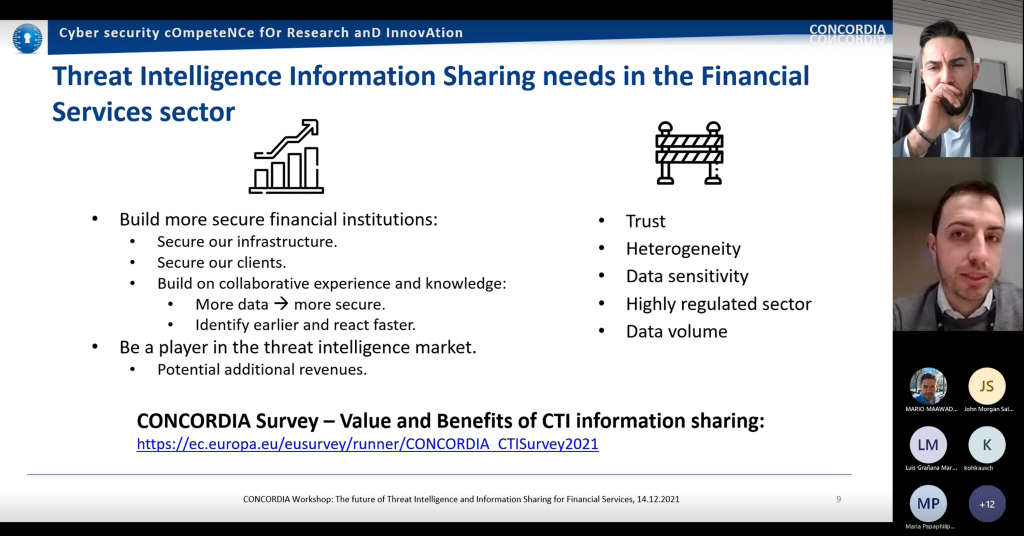
Wide support from ecosystem stakeholders (e.g. development of new MISP modules, integration with the clearing house, operational support etc), or adoption by relevant users, seems not only desirable, but also necessary, in order to bring this project result to the market. The more you share, more benefit there is, looks like a straightforward and intuitive message, but hard to measure quantitatively and qualitatively. This is also the reason why tried to analyze economic impact of cybersecurity threat intelligence sharing in financial sector.
Several categories of costs related to data sharing exist in general, clustered into strategic (e.g. investment decision making), tactical (e.g. selection and implementation of platform) and operational (e.g. filtering of applicable data). In practice, however, benefits are more difficult to categorize or measure. What are the parameters that impact the benefits of sharing? Number of overall entities that participate in a sharing scheme? Number of entities with similar threat context? Data timeliness, trustworthiness, completeness, or accuracy?
It is difficult to separate the benefits of different layers of security controls. It is, however, sometimes possible to measure reduction of time needed to identify and resolve an incident, and to attribute this reduction to threat intelligence sharing.
We tried to measure how “timeliness” of Financial CTI sharing, changes the perspective of the economic impact of an attack in an organization, often linked to “time to react”. In case of our simulation the attack was related to a previously unknown phishing attack. For the situation when threat data is shared only one hour before the attack on the next entity occurs, which implies that it might not be fully actionable intelligence, or that all response measures are still not in place, we still find a reduction of damage between 7% and 10%. In the case that information is shared and received more than 40 hours before attack on a financial entity occurs, which is a much more likely situation, damage is reduced significantly, almost to 85% of what would have been the size of damage initially, without use of threat intelligence.
We should also mention that “timeliness” as an indicator of economic value of cybersecurity threat intelligence sharing, varies slightly if we look at the different types of data sources.
In collaboration between WP2 and WP5, we have prepared an event with the financial sector stakeholders in December 2021 and have launched survey about importance of “timeliness” of sharing in a wide range of data and intelligence sources. In the case of internal threat intelligence sources (helpdesk, parsing data from firewall, SIEM, IDS/IPS…), importance of timeliness scored 4.6 (with 5 being highest score). Timeliness of data and intelligence being received through external structured sources (Vulnerability databases, IP address blacklisting and whitelisting etc) was judged as slightly less important (4) while the lowest score (3.6) was given to external unstructured sources (usually based on natural language processing and crawlers that extract data text found on darkweb, forums, social networks, news etc). In future we plan to extend this study and to receive more feedback on possible benefits, including relevant insights in decisive factors for adoption of cybersecurity threat intelligence sharing strategies in an organization.
(By: Aljosa Pasic (ATOS) and Mario Mawaad (Caixabank))