Cloud Security: Paving the Way to Smarter Security Automation!
Cloud is everywhere, often invisible…
The development of the Internet has been leveraged by the deployment of large data centers providing computing resources (software application, virtualized hardware equipment) that can be shared and combined to build elaborated services. These resources available in a metered manner are contributing to lower the operational costs of infrastructures and their services. In particular, cloud computing introduces new service models (i.e. Infrastructure-as-a-Service, Platform-as-a-Service, Software-as-Service) that facilitate the usage and configuration of these resources. In that context, cloud service providers may offer multiple types of resources, with various levels of manageability and security, that can be exploited and composed by customers.
… and highly exposed to security attacks
As they are available through broad network access, cloud resources constitute an attractive target for hackers and cyber-criminals. They are concerned by a large variety of security attacks, that are orchestrated in a more or less stealthy manner. These resources are often distributed over several cloud providers and may be shared amongst different customers based on multi-tenancy models, causing isolation issues. They are also more exposed to service disruption attacks due to their on-demand self-service provisioning. The dependencies amongst these resources may also permit the access and alteration of them by unauthorized parties due to improper access control. These security attacks are gaining in sophistication and coordination (i.e. advanced persistent threats, usage of artificial intelligence), and may affect the fundamental security goals of confidentiality, integrity, availability and non-repudiation of cloud resources.
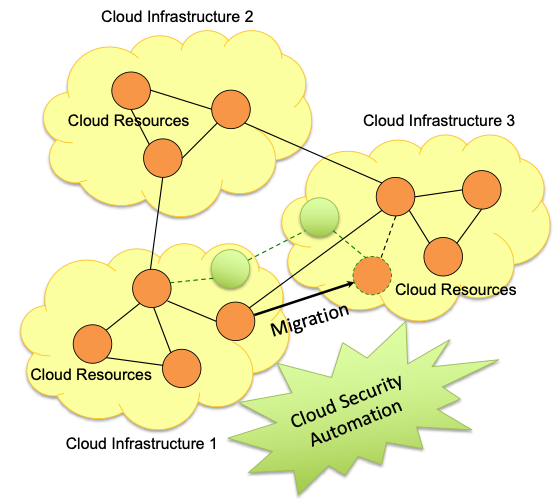
The challenge of smarter security automation
A part of our scientific job in CONCORDIA aims paving the way to smarter security automation for preventing, detecting and mitigation security attacks, in particular in the case of complex cloud services. These services are typically constructed from elementary cloud resources that are distributed over several cloud infrastructures and are subject to changes and updates over time, such as the migration of a cloud resource from one cloud infrastructure to another one. We are investigating novel methods and techniques capable to cope with the properties of these cloud services in terms of distribution, dynamics and complexity. Developing smarter security automation enables to bring more timely, more adequate, and more effective responses to current and future security threats, by preventing cyber storms in the cloud.
References
- P. Mell, T. Grance, The NIST Definition of Cloud Computing, NIST SP800-145, September 2011.
- Cloud Security Alliance, Top Threats to Cloud Computing: Egregious Eleven, June 2019.
- R. Badonnel, C. Fung, Q. Li and S. Scott-Hayward, “Guest Editorial: Special Section on Cybersecurity Techniques for Managing Networked Systems,” in IEEE Transactions on Network and Service Management, vol. 17, no. 1, pp. 12-14, March 2020, doi: 10.1109/TNSM.2020.2972769.
- M. Compastie, R. Badonnel, O. Festor, R. He: From Virtualization Security Issues to Cloud Protection Opportunities: An In-depth Analysis of System Virtualization Models. Computers & Security. 97: 101905 (2020).
(By Mohamed Oulaaffart, Rémi Badonnel, Olivier Festor, University of Lorraine)
