CONCORDIA’s Incident Clearing House: a Closer Look
In this blog post we are going to have a closer look at one of the core components of CONCORDIA’s Threat Intelligence Platform: the Incident Clearing House. What does it do? How does it work? And how does it integrate with the other platform components?
A Core Component
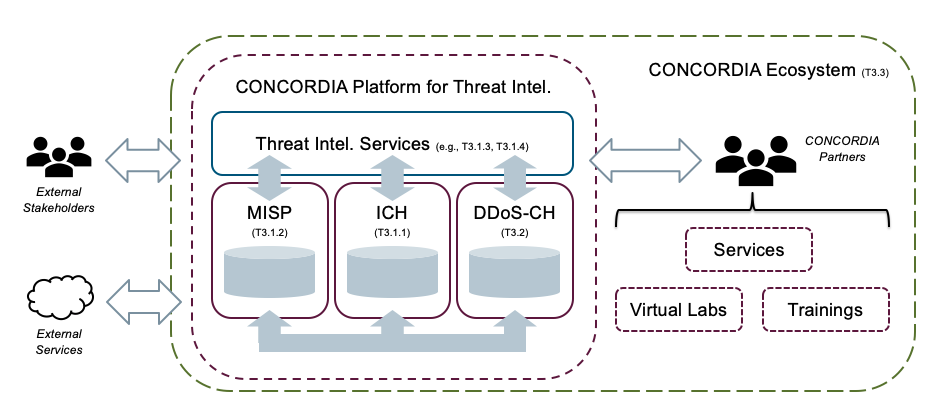
The Incident Clearing House is part of CONCORDIA’s Threat Intelligence Platform, which was previously described on this blog. Together with MISP and the DDoS Clearing House it is one of the three core components of the platform as seen below.
In this platform, the Incident Clearing House or ICH fulfils a complementary function to the usual meaning of threat intelligence sharing. While this often refers to sharing information on things that might come your way, so you can be on the lookout, the ICH informs you of problems that have already been detected in your network by someone else.
Data to Clean Your Network
An illustrative example of this is information about a botnet. When analysing a botnet there are different sets of information that can be collected, like
- information on the botnet’s command and control infrastructure,
- indicators pointing to an infection with the bot malware (so-called Indicators of Compromise or IoCs), or
- a list of already compromised systems that contact the botnet’s command and control infrastructure.
The first two kinds of information belong to the classic realm of threat intelligence sharing. They are submitted to platforms like MISP to inform every connected party of things to watch for to prevent infections in their network or detect them if they already happened. Information on the compromised systems, the bots, on the other hand, is mainly useful for the owners of these systems. And they can be reached by sharing the data via the ICH, which forwards the information to the registered owners of the corresponding networks.
The ICH Architecture
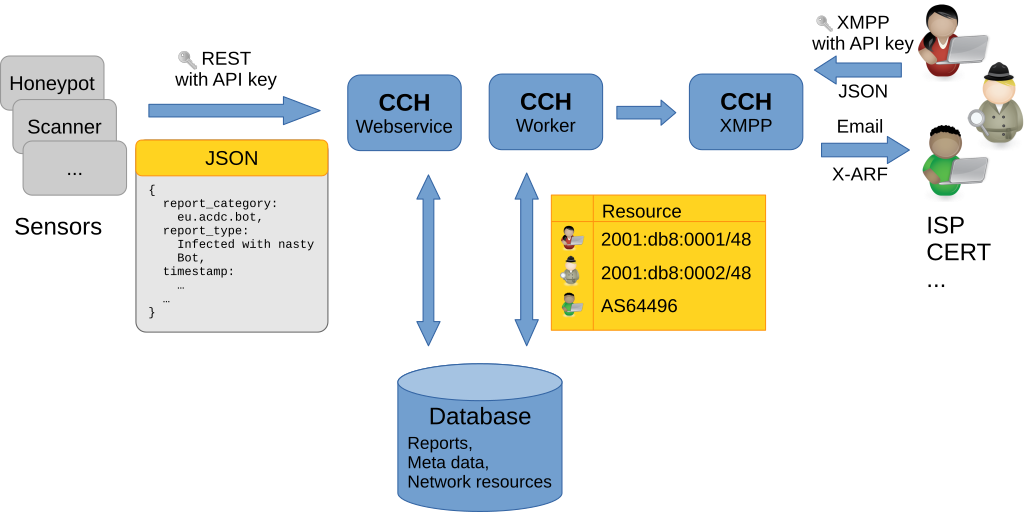
But how does the ICH work internally. For that have a look at the following overview of the ICH architecture.
Data is submitted to the ICH via a REST API using a defined JSON format. These reports can come from different sources like honeypots, scanners, or sinkholes. Once in the ICH, separate worker processes take over and match the reports to the corresponding network resources previously registered for the different parties connected to the ICH. These parties then get access to exactly the reports that have been submitted for their network resources.
Connecting to an Eco System
The current list of participants to the ICH includes mainly the CERT community organised in the TF-CSIRT group. To expand this list and to ease access to the complete Threat Intelligence Platform, work is ongoing in CONCORDIA between the core component providers and legal partners to define a unified Code of Engagement.
But the threat intelligence platform is not only three separate core components. Work is also proceeding on interactions between the components as described in the blog post on the platform mentioned above. One of the first additional services we build on top of the core components is a metric generation and anomaly detection that supports an overview of current and emerging threats based on the data submitted to the platform.
That concludes our tour of the Incident Clearing House: one of the core components in CONCORDIA’s Threat Intelligence Platform and its role in making the internet a little more secure.
(By Dr.-Ing. Christian Keil, DFN-CERT Services GmbH)