Enhancing Hardware Security in IoT/Embedded Systems
In an ever-expanding and fully connected world of device-centric solutions, a significant amount of IoT/Embedded systems has been deployed in a plethora of environments. This adaptation of the recent advancements of the technological field in Embedded systems these recent years can be evaluated as quite hasty, focusing mainly on performance capabilities alone, disregarding important security features. Their widespread adoption, the easy physical access as well as the inherent resource constraints for proper countermeasures, make these systems a prime target for a physical attack.
Flexible solutions that provide strong countermeasures are, thus, required in order to protect IoT/Embedded systems from a wide range of physical attacks. The designed protection mechanisms should be evaluated and if possible updated based on emerging types of attacks, as well as being adopted on more cryptographic primitives.
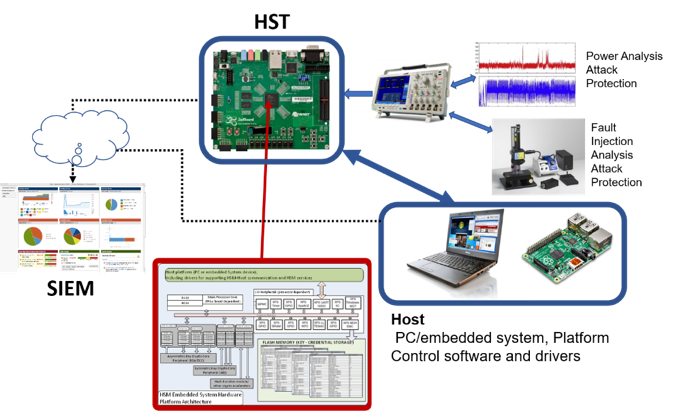
Through this scope, promoting the migration of the security functions in Hardware without compromising QoS is an essential step towards a Security-by-Design approach. As an example of such an approach, we can mention dedicated, secure and trusted solutions that provide a holistic security level by using hardware and software means, like Hardware Security Modules. In CONCORDIA, the University of Patras and the Industrial Systems Institute/research Center ATHENA will collaborate in order to provide a Hardware Security Token (HST) solution that will act as a self-contained secure environment solution for a wide range of cryptographic/ security needs and with provide highly scalable features independent from the IoT/Embedded system in need of protection. This solution can be utilized in industrial and cyber-physical system applications and will be used in the CONCORDIA pilots as a secure infrastructure/environment for security/trust services.
Evaluating Security of Cryptography Implementations with Machine Learning
Hardware security Tokens are highly vulnerable from badly implemented cryptography solutions in hardware or software due to leakages of information from physical characteristics of the hardware itself. The various physical leakages that happen during a cryptographic algorithm execution can contain critical information that is exploited by a process known as Side Channel Analysis (SCA). A very powerful form of SCA attack, the so-called Profiling attack, requires a clone device in order to generate a “profile” for the target. This profiling phase is realized through the collection of sample template traces (EM radiation, power consumption) from the identical device during a cryptographic execution.
In CONCORDIA, the University of Patras and the Industrial Systems Institute/research Center ATHENA collaborate and explore the recent trend in use of supervised Machine Learning classification algorithms for SCAs since such algorithms can provide a stronger target device profile generation mechanism compared to classic profile attacks based on templates. In recent literature, the most commonly used supervised ML algorithms that enable SCA attacks have been Support Vector Machines (SVMs), Rotation Forest (RF) along with Naive Bayes (NB) and the Multi-Layer Perceptron (MLP). Additionally, Convolutional Neural Networks (CNNs) offer great accuracy in cases with low noise level and high number of available traces.
The majority of these algorithms show promising results compared to the statistical methods of template and stochastic attacks, paving the way for novel techniques and security countermeasure implementations.
As an overall goal, the University of Patras and the Industrial Systems Institute/research Center ATHENA will establish, in CONCORDIA, an elaborate testing platform can act as a Security Research Playground, enabling us to launch Machine Learning based attacks on cryptographic implementations. This assessment of the security level of the operating cryptographic protocols can help us introduce or enhance attack countermeasures to the HST.
Authors:
Charis Dimopoulos, University of Patras, Greece
Dr. Apostolos P. Fournaris, Industrial Systems Institute, Greece
