Integration of MISP into Flowmon ADS
In this document, we will describe the integration of the MISP platform and the Flowmon Anomaly Detection System. The purpose of this integration is to automatically detect a threat in the network using indicators of compromise provided via an instance of the MISP platform connected to Flowmon.
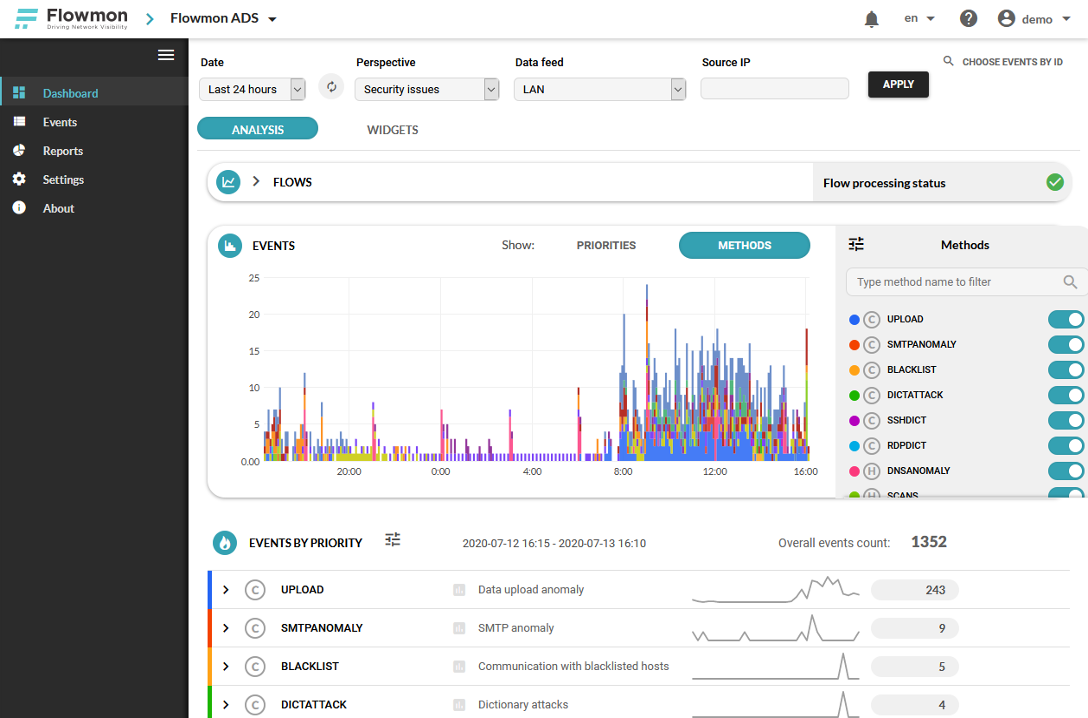
One of the products from Flowmon Networks is Anomaly Detection System (ADS) which is responsible for detecting unwanted and potentially harmful communication inside the computer network. In general, the ADS is permanently analyzing the transferred data with a set of detection methods. When any of the methods detect an anomaly an appropriate event is generated. Figure 1 shows a chart showing the amount of detected events for the last 24 hours where each color represents one method. Below the chart are events organized into a list format, where it’s possible to go more deep inside the detected events (e.g., shows which devices were involved).
In this text, we will work with an ADS method called “Blacklists” which is responsible for detecting a predefined list of IoCs within the network traffic. IoC is an acronym for “Indicator of Compromise” and it can be described as a fingerprint of a specific potentially malicious activity. The fingerprint can have several forms, for example, IP address, domain name, URL, or a hash of a specific file. By detecting a specific IoC inside the network, it’s possible to say (with some confidence) that the same malicious activity (for which the IoC was created) has been detected. IoCs are usually created and maintained by analytical teams that share information with other teams to increase the security of computer systems.
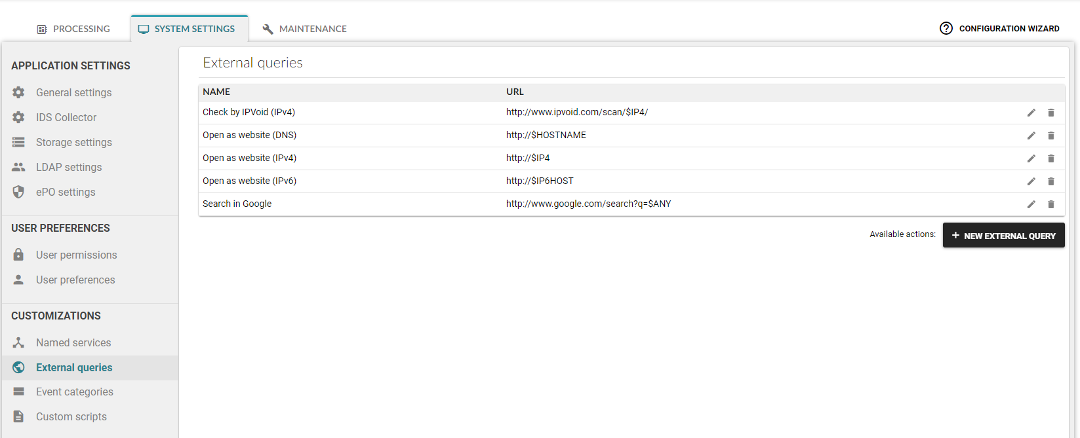
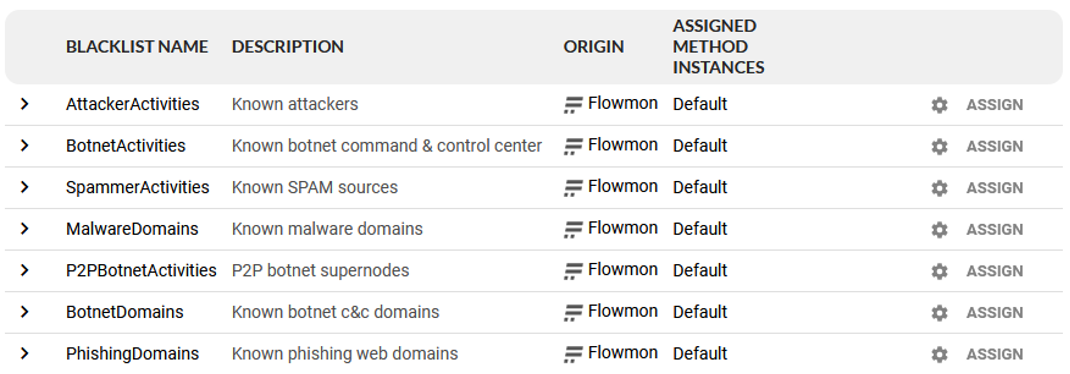
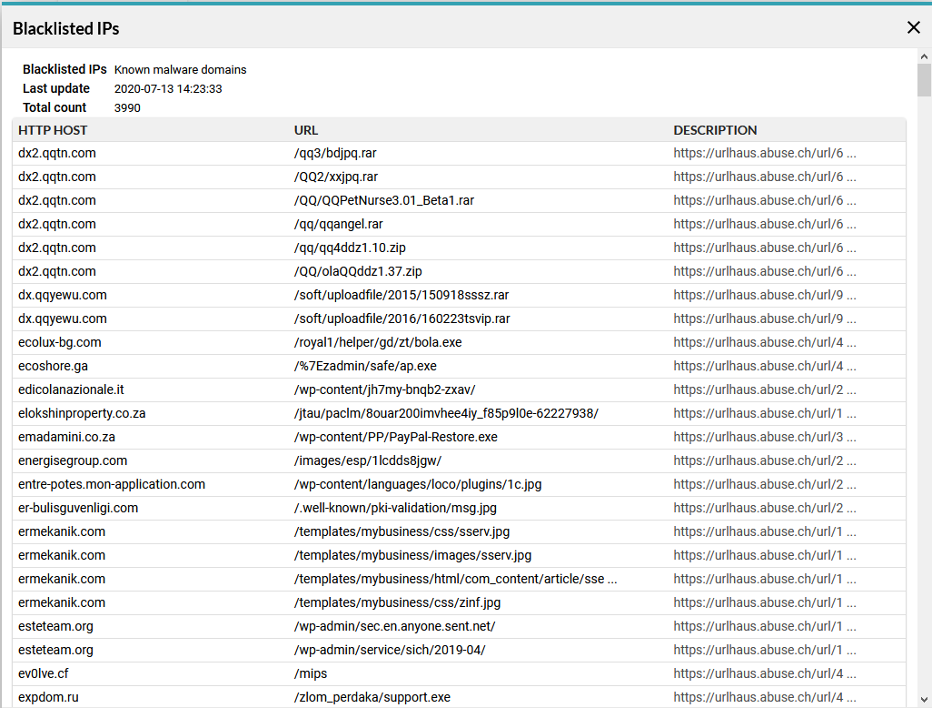
In the Flowmon ADS, multiple sources of IoCs are predefined by default and provided by Flowmon Networks. The actual list is shown in Figure 2. Each source is specific to some specific security threat (or category of threats), e.g., a list of known malware domains. It’s also possible to add custom sources of IoCs for extending the capability of threat detection. The content of each blacklist can also be checked as shown in Figure 3.
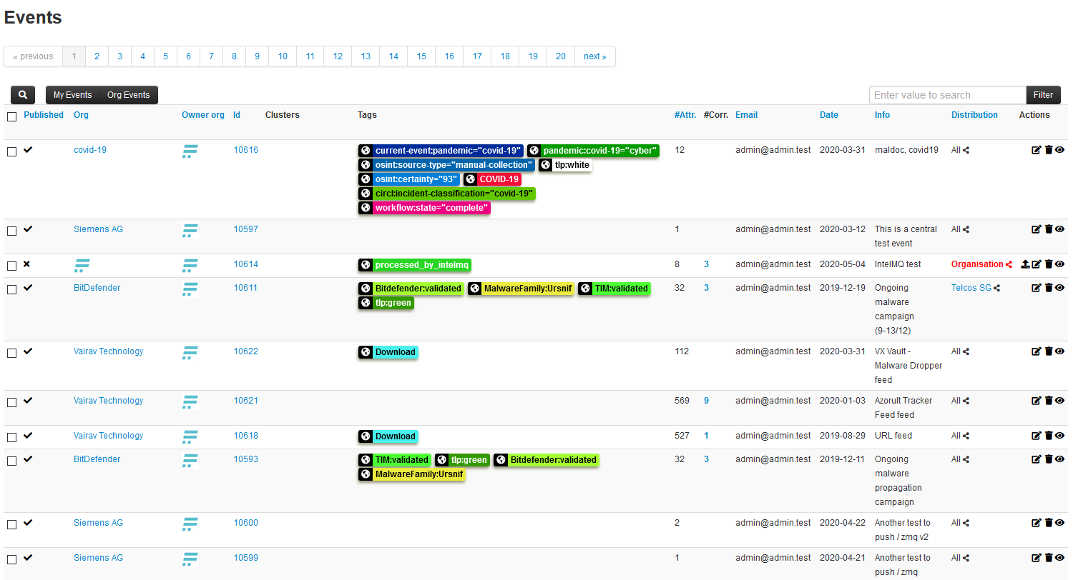
There are many ways of how the IoCs can be shared between users, e.g., publishing them on websites, providing specific data feeds for downloads, or specific API. One such approach is by using a platform called MISP. MISP is an open-source platform for sharing IoCs which development is supported by the European Union. MISP allows creating a big knowledge database based on data from multiple independent analytical teams across multiple companies. This knowledge can afterward be used by network administrators and monitoring tools to increase the security of the networks. An example of MISP content can be seen in Figure 4 which shows a list of defined events.
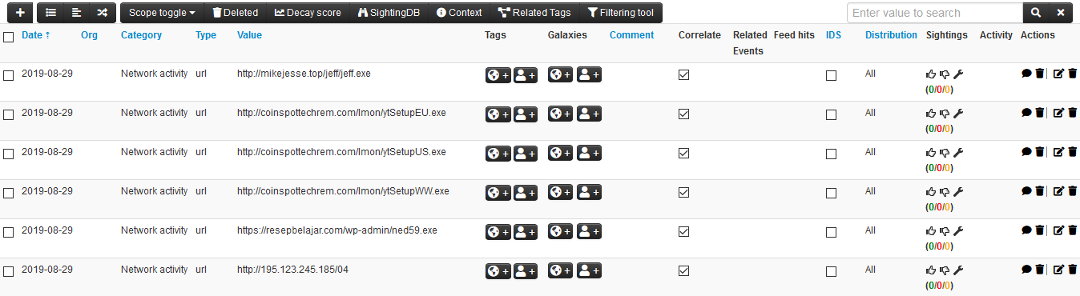
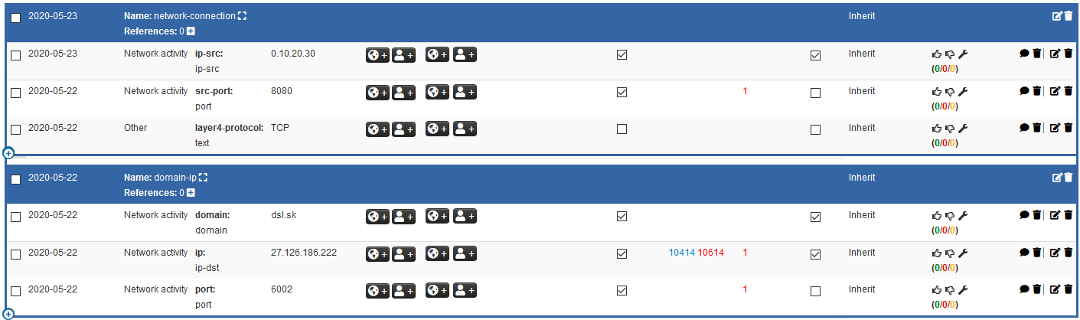
Each MISP event consists of multiple IoCs which can be used for detecting potentially malicious activities. An example of event content is shown in Figure 5. The figure shows a list of IP addresses that were defined by the AZORult malware tracker. An event can also consist of more complex objects which describe IoCs in more detail. E.g., in figure 6, there are two objects which specify not just IP addresses or domain names, but also transport protocols and ports.
We have created an integration of the MISP platform into Flowmon ADS, so it’s possible to use IoCs defined in MISP to detect threats and attacks in customer-specific environments. So for example, if an analysis team connected into Concordia’s MISP platform will detect a new threat, the team creates a new IoC which will describe the threat and share the threat with the community. Any community member running MISP connected to Concordia MISP instance is able to receive an update of IoCs and provide that IoCs automatically to his instance of Flowmon ADS to detect and report such threat in his network environment.
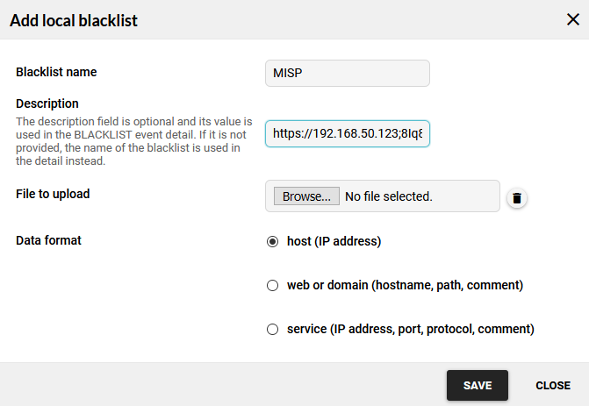
To use MISP as the source of data, it’s necessary to know the IP address of the server, API key, and possibly event_tag. IP address and the API key are needed to establish a successful connection. The event_tag is an optional parameter that specifies which events from the server should be used. By using this tag, it’s possible to select only a subset of events that should be used. This is useful if some events are very sensitive or they just don’t contain any relevant data. If no tag is specified, all events from MISP are used. All three mentioned parameters are specified under the Add local blacklist section, field Description. Additionally to the name, the data format needs to be specified as well. This data format specifies which IoC will be used. In the future, we will remove this selection so all data formats will be downloaded at once in the case of the MISP data source. Figure 7 shows the definition of a new MISP server as a data source for Flowmon ADS.
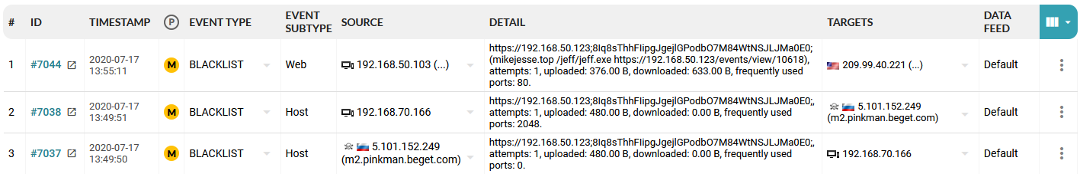
After the MISP platform is integrated into the Flowmon ADS, it’s possible to detect harmful or dangerous traffic by checking if any of the network traffic matches any of the patterns defined by IoCs from the MISP. This situation is demonstrated in Figure 8, where two events (events from the anomaly detection system, not MISP events) are shown. Each event describes that communication with potentially dangerous IP addresses (column Source) occurred in the network.
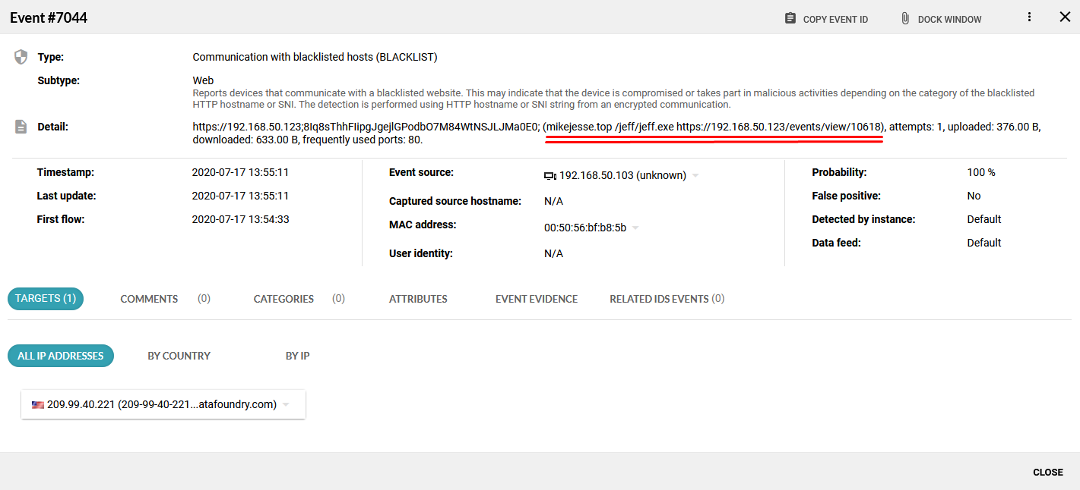
It’s also possible to display detailed information about the detected event. In Figure 9, it’s possible to see the which IP address was communicating with a blacklisted IP address (Event source), which IoC has been detected and the link to the MISP platform (Detail).
(By Pavel Minarik, Flowmon Networks)