Towards Context-based Vulnerability Analysis & Inference Lancaster University
Over the last decade, a conspicuous increase in the number of vulnerabilities coupled with a paucity of detailed information about them has hindered qualified vulnerability analysis, and consequently, resulted in multiple outstanding vulnerabilities in the wild. Fig. 1 illustrates the number of vulnerabilities reported in 2019. For instance, in January alone, over a 1000 vulnerabilities with a medium severity level (Common Vulnerability Scoring System (CVSS) of above 5) were reported. Thus, significant manpower is required to analyze each disclosed vulnerability and consequently assess its potential impact on a system.
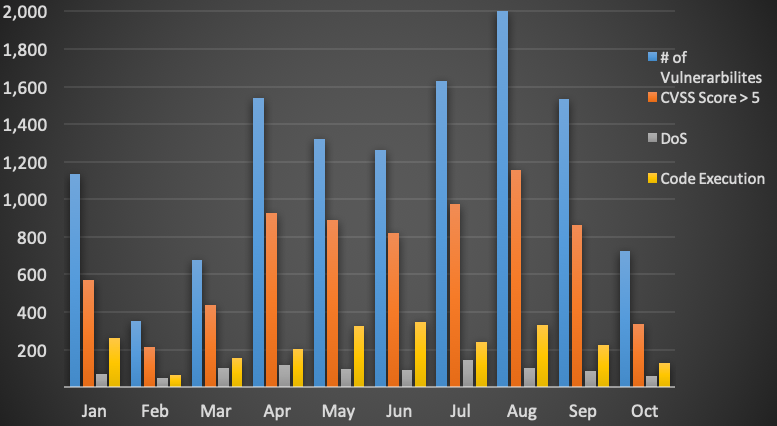
In order to facilitate security analysts, a range of knowledge bases exists to assist security analysts in taking an informed decision about a vulnerability. Among the commonly used knowledge base is the National Vulnerability Database (NVD) that enumerates vulnerability characteristics such as attack surface, vulnerability impact and severity categorization among many others. Furthermore, NVD classifies vulnerabilities into abstract classes using their likely disruption consequences as a criterion for the classification. For instance, a vulnerability is assigned to the class of Denial of Service (DoS) if it disrupts the service. A code execution class gets assigned if it allows an attacker to execute malicious code on the victim machine. Fig. 1 depicts these classes as well as the respective number of reported instances in each class. On the other hand, the classification, using only consequence as the sole parameter, limits the fine-grained and meaningful evaluation of vulnerabilities interconnections. Overall, in its current form, the state of the art databases fail to reveal the subtle interconnected patterns among the vulnerabilities and facilitate the systematic reasoning regarding vulnerability’s potential variants.
To fill this gap, as a part of the CONCORDIA project, our objective is to develop mechanisms to explore correlation among the vulnerabilities to reveal common Indicator of Compromise (IoC) and the degree of correlation among these indicators. The low-level indicators comprise of malware hash values, IP addresses, etc., exhibit static properties as the contextual information about the attack is not required for these IoC. However, for the high-level IoC (e.g., attack surface, tactics, techniques, procedures, etc.) the context of an attack is critical to appropriately comprehend the high-level IoC. We term them as behavioral properties of the vulnerability. In order to accomplish this detailing, it is necessary to create a model of the vulnerability context by incorporating both the static and behavioral properties. The challenge here is to extract these properties from the dispersed, isolated and scattered pieces of information available about the vulnerability. To achieve this, we perform lexical analysis and extract both static and behavioral characteristics to create a vulnerability context that becomes the basis for evaluating correlations among the vulnerabilities.
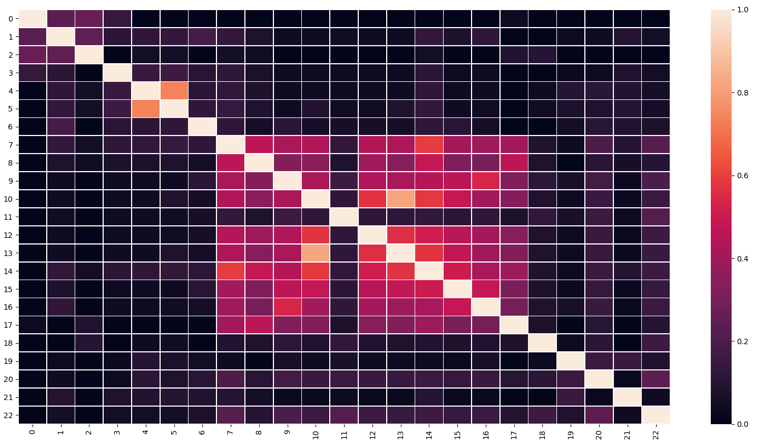
Fig. 2 depicts the contextual similarity among a small subset of vulnerabilities. For instance, vulnerability # 10 (CVE-2014-8578) and vulnerability # 13 (CVE-2014-3475) exhibit similar semantics with respect to the attack mechanism, targeted system, etc. The only difference is the interface where the attack mechanism is applied. Thus, these vulnerabilities are clustered together and in the presence of vulnerability # 10, the system must be checked for the other vulnerability. Moreover, context-based assessment enables the system administrator to infer further vulnerabilities exhibiting similar attack patterns.
On the other hand, we can also delve into exploring attackers’ preferred mechanisms against their profiles and expertise, e.g., script kiddies, state-sponsored attackers, etc. This is achieved by analyzing specific attack mechanisms exploiting certain systems to elaborate on the applicability of these attacks. This leads to system hardening against varied attacker profiles by mitigating “common” attack mechanisms. For instance, system security can be hardened against cross-site scripting attacks by mitigating its “all” common attack mechanism that can be used to undermine the security of the system. Thus, mitigating attack mechanisms forces attackers to find a new and innovative mechanism to exploit the system.
In summary, vulnerability inference based on a context reveals patterns that are useful in evaluating the security of the system holistically by identifying and mitigating a class of vulnerabilities across different layers and varied attacker profiles. Correspondingly, it supports cost-effective security management of the system by identifying the critical cluster of vulnerabilities to patch.
(by Salman Manzoor, Technical University of Darmstadt)
