Performing excellent academic research is the essential objective of the CONCORDIA project.
Our research activities are organized into five tasks, each focusing on a particular aspect of cybersecurity.
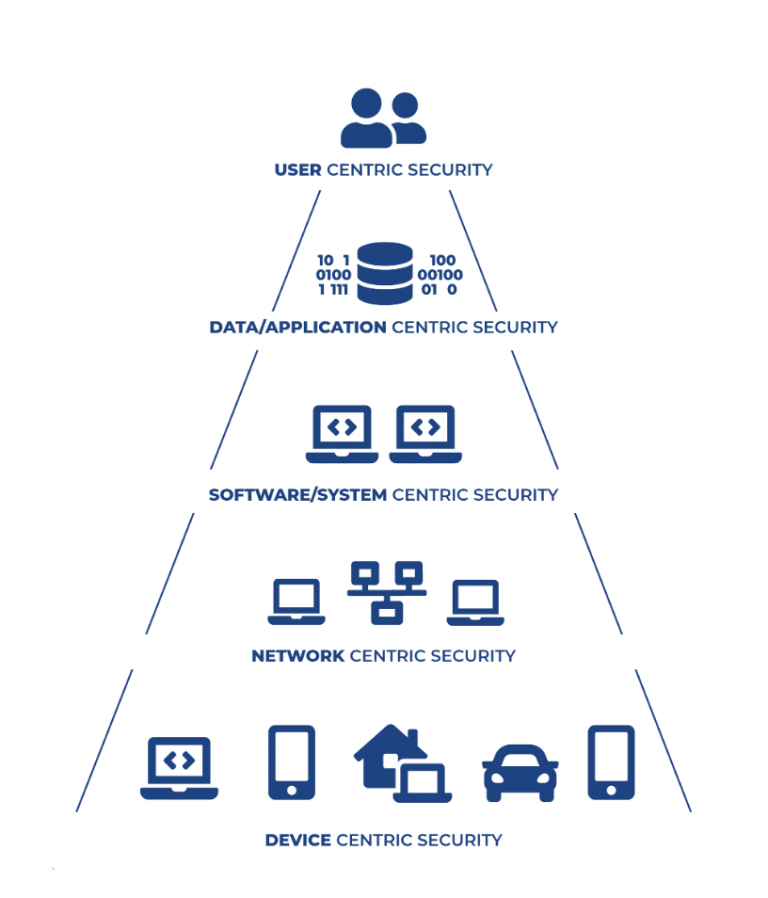
During the project’s lifetime, we produced 324 publications. The total number of papers entered into the EU-ECAS system is even higher since white papers and papers without peer review are not counted. You can find all our publications on our website.
| Security Aspects | 2019 | 2020 | 2021 | 2022 | Total |
| Device | 10 | 23 | 19 | 25 | 77 |
| Network | 9 | 30 | 15 | 20 | 74 |
| Software and system | 8 | 13 | 4 | 7 | 32 |
| Data and application | 16 | 15 | 18 | 12 | 61 |
| User security and privacy | 16 | 26 | 20 | 18 | 80 |
| Total | 59 | 107 | 76 | 82 | 324 |
Here we present only our selection. Selected publications are all journal papers with SJR >= 2.0 and all CORE A* conference papers (excluding poster and demo papers).
- P. Colombo, E. Ferrari, E.D. Tümer (UI): Regulating data sharing across MQTT environments. Elsevier Journal of Network and Computer Applications, 174, January 2021 https://doi.org/10.1016/j.jnca.2020.102907 [D1.2, SJR 2.19]
- A.S. Lalos, E. Vlachos, K. Berberidis, A.P. Fournaris, C. Koulamas (ISI): Privacy Preservation in Industrial IoT via Fast Adaptive Correlation Matrix Completion. IEEE Transactions on Industrial Informatics 16(12), 2020 https://doi.org/10.1109/TII.2019.2960275 [D1.2, SJR 4.33]
- I. Ahmed, M. Anisetti, A. Ahmad, G. Jeon (UMIL): A Multilayer Deep Learning Approach for Malware Classification in 5G-Enabled IIoT. IEEE Transactions on Industrial Informatics, 2022 https://doi.org/10.1109/TII.2022.3205366 [D1.4, SJR 4.33]
- E. Schiller, A. Aidoo, J. Fuhrer, J. Stahl, M. Ziörjen, B. Stiller (UZH): Landscape of IoT Security. Elsevier Computer Science Review 44, May 2022 https://doi.org/10.1016/j.cosrev.2022.100467 [D1.4, SJR 2.562]
- A. Khurshid, S. D. Yalew, M. Aslam, S. Raza (RISE): ShieLD: Shielding Cross-zone Communication within Limited-resourced IoT Devices running Vulnerable Software Stack IEEE Transactions on Dependable and Secure Computing, 2022 https://doi.org/10.1109/TDSC.2022.3147262 [D1.4, SJR 2.265]
- Y. Meidan, D. Avraham, H. Libhaber, A. Shabtai (BGU): CADeSH: Collaborative Anomaly Detection for Smart Homes. IEEE Internet of Things Journal, 2022 https://doi.org/10.1109/JIOT.2022.3194813 [D1.4, SJR 3.848]
- Y. Sharon, D. Berend, Y. Liu, A. Shabtai, Y. Elovici (BGU): TANTRA: Timing-Based Adversarial Network Traffic Reshaping Attack. IEEE Transactions on Information Forensics and Security 17, 2022 https://doi.org/10.1109/TIFS.2022.3201377 [D1.4, SJR 3.299]
- M. Hamad, A. Finkenzeller, H. Liu, J. Lauinger, V. Prevelakis, S. Steinhorst (TUBS): Secure Endto-End MQTT-Based Communication for Mobile IoT Systems Using Secret Sharing and Trust Delegation. IEEE Internet of Things Journal, November 2022 https://doi.org/10.1109/JIOT.2022.3221857 [D1.4, SJR 3.848]
- H. Lee, A. Gireesh, A.V. Vidyapeetham, R.v. Rijswijk-Deij, T. Kwon, T. Chung (UT): A Longitudinal and Comprehensive Study of the DANE Ecosystem in Email. Proceedings of the USENIX Security Symposium, 2020 USENIX Association [D1.2, CORE A*]
- E. Papadogiannaki, S. Ioannidis (FORTH): A Survey on Encrypted Network Traffic Analysis Applications, Techniques, and Countermeasures. ACM Computing Surveys 54(6), 2021 https://doi.org/10.1145/3457904 [D1.3, SJR 5.090]
- E.J. Scheid, B. Rodrigues, B. Stiller (UZH): Policy-Based Blockchain Selection. IEEE Communications Magazine 59(10), October 2021 https://doi.org/10.1109/MCOM.100.2100120 [D1.3, SJR 5.147]
- A.S.M. Rizvi, L. Bertholdo, J. Ceron, J. Heidemann (UT, SIDN): Anycast Agility: Network Playbooks to Fight DDoS. Proceedings of the 31st USENIX Security Symposium, August 2022 USENIX Association [D1.4, CORE A*]
- H. Lee, Md.I. Ashiq, M. Müller, R. van Rijswijk-Deij, T. Kwon, T. Chung (UT, SIDN): Under the Hood of DANE Mismanagement in SMTP. Proceedings of the 31st USENIX Security Symposium, August 2022 USENIX Association [D1.4, CORE A*]
- T. Arnold, E. Gürmeri.liler, G. Essig, A. Gupta, M. Calder, V. Giotsas, E. Katz-Bassett (ULANC): (How Much) Does a Private WAN Improve Cloud Performance? IEEE Conference on Computer Communications (INFOCOM), 2020 https://doi.org/10.1109/INFOCOM41043.2020.9155428 [D1.2, CORE A*]
- B. Cheng, J. Ming, E. Leal, H. Zhang, J. Fu, G. Peng, J.-Y. Marion (UL): Obfuscation-Resilient Executable Payload Extraction From Packed Malware. Proceedings USENIX Security, February 2021 USENIX Association [D1.3, CORE A*]
- P. Colombo, E. Ferrari (UI): Evaluating the effects of access control policies within NoSQL systems. Elsevier Future Generation Computer Systems 114, January 2021 https://doi.org/10.1016/j.future.2020.08.026 [D1.2, SJR 2.23]
- F. Daidone, B. Carminati, E. Ferrari (UI): Blockchain-based Privacy Enforcement in the IoT Domain. IEEE Transactions on Dependable and Secure Computing, September 2021 https://doi.org/10.1109/TDSC.2021.3110181 [D1.3, SJR 2.265]
- M. Sestak, M. Hericko, T. Welzer Druzˇovec, M. Turkanovic (UM): Applying k-vertex cardinality constraints on a neo4j graph database. Elsevier Future Generation Computer Systems, February 2021 https://doi.org/10.1016/j.future.2020.09.036 [D1.3, SJR 2.233]
- M. Anisetti, C. A. Ardagna, N. Bena (UMIL): Multi-Dimensional Certification of Modern Distributed Systems. IEEE Transactions on Services Computing, 2022 [D1.4, SJR 2.714]
- P. Papadopoulos, N. Kourtellis, E. Markatos (FORTH, TID): Cookie synchronization: Everything you always wanted to know but were afraid to ask. Proceedings of the World Wide Web Conference (WWW). May 2019 https://doi.org/10.1145/3308558.3313542 [D1.1, CORE A*]
- S. Zannettou, T. Caulfield, E. De Cristofaro, M. Sirivianos, G. Stringhini, J. Blackburn (CUT): Disinformation Warfare: Understanding State-Sponsored Trolls on Twitter and their Influence on the Web. Companion Proceedings of The 2019 World Wide Web Conference, May 2019 https://doi.org/10.1145/3308560.3316495 [D1.1, CORE A*]
- P. Agarwal, S. Joglekar, P. Papadopoulos, N. Sastry, N. Kourtellis (TID): Stop tracking me Bro! Differential Tracking of User Demographics on Hyper-Partisan Websites. Proceedings of The Web Conference 2020, April 2020 https://doi.org/10.1145/3366423.3380221 [D1.2, CORE A*]
- H. Herodotou, Despoina Chatzakou, N. Kourtellis (TID, CUT): Catching them red-handed: Realtime Aggression Detection on Social Media. Proceedings of the International Conference on Data Engineering (ICDE), June 2020 https://doi.org/10.1109/ICDE51399.2021.00211 [D1.2, CORE A*]
- M. Diamantaris, S. Moustakas, L. Sun, S. Ioannidis, J. Polakis (FORTH): This Sneaky Piggy Went to the Android Ad Market: Misusing Mobile Sensors for Stealthy Data Exfiltration. ACM SIGSAC Conference on Computer and Communications Security (CCS ’21), November 2021 https://doi.org/10.1145/3460120.3485366 [D1.3, CORE A*]
- A.-T. Hoang, B. Carminati, E. Ferrari (UI): Privacy-Preserving Sequential Publishing of Knowledge Graphs. Proceedings of the IEEE International Conference on Data Engineering (ICDE), 2021 https://doi.org/10.1109/ICDE51399.2021.00194 [D1.3, CORE A*]
- E. Papadogiannakis, P. Papadopoulos, N. Kourtellis, E.P. Markatos (TID): User Tracking in the Post-cookie Era: How Websites Bypass GDPR Consent to Track Users. Proceedings of the Web Conference 2021, WWW ’21, April 2021. https://doi.org/10.1145/3442381.3450056 [D1.3, CORE A*]
- C. Sandeepa, B. Siniarski, N. Kourtellis, S. Wang, M. Liyanage (TID): A survey on privacy for B5G/6G: New privacy challenges, and research directions. Journal of Industrial Information Integration 30, November 2022 https://doi.org/10.1016/j.jii.2022.100405 [D1.4, SJR 2.745]
- E. Papadogiannakis, P. Papadopoulos, E.P. Markatos, N. Kourtellis (TID, FORTH): Leveraging Google’s Publisher-Specific IDs to Detect Website Administration. Proceedings of the ACM Web Conference, April 2022 https://doi.org/10.1145/3485447.3512124 [D1.4, CORE A*]

